Wireshark 2 Quick Start Guide: Secure your network through protocol analysis 1, Mishra, Charit, eBook - Amazon.com

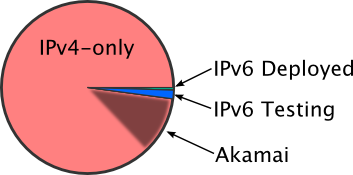
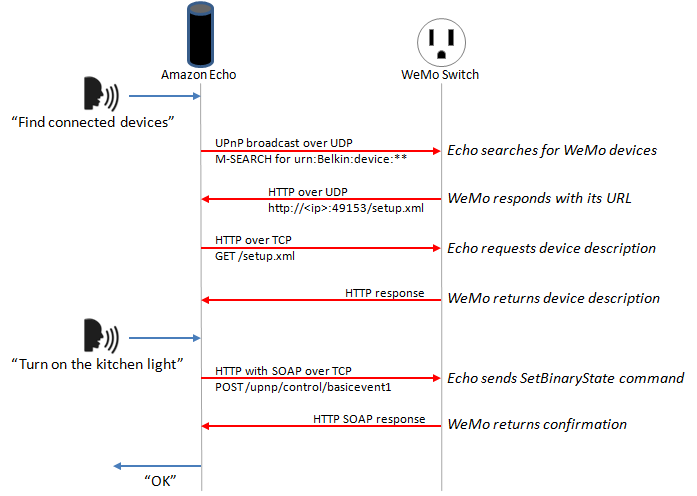
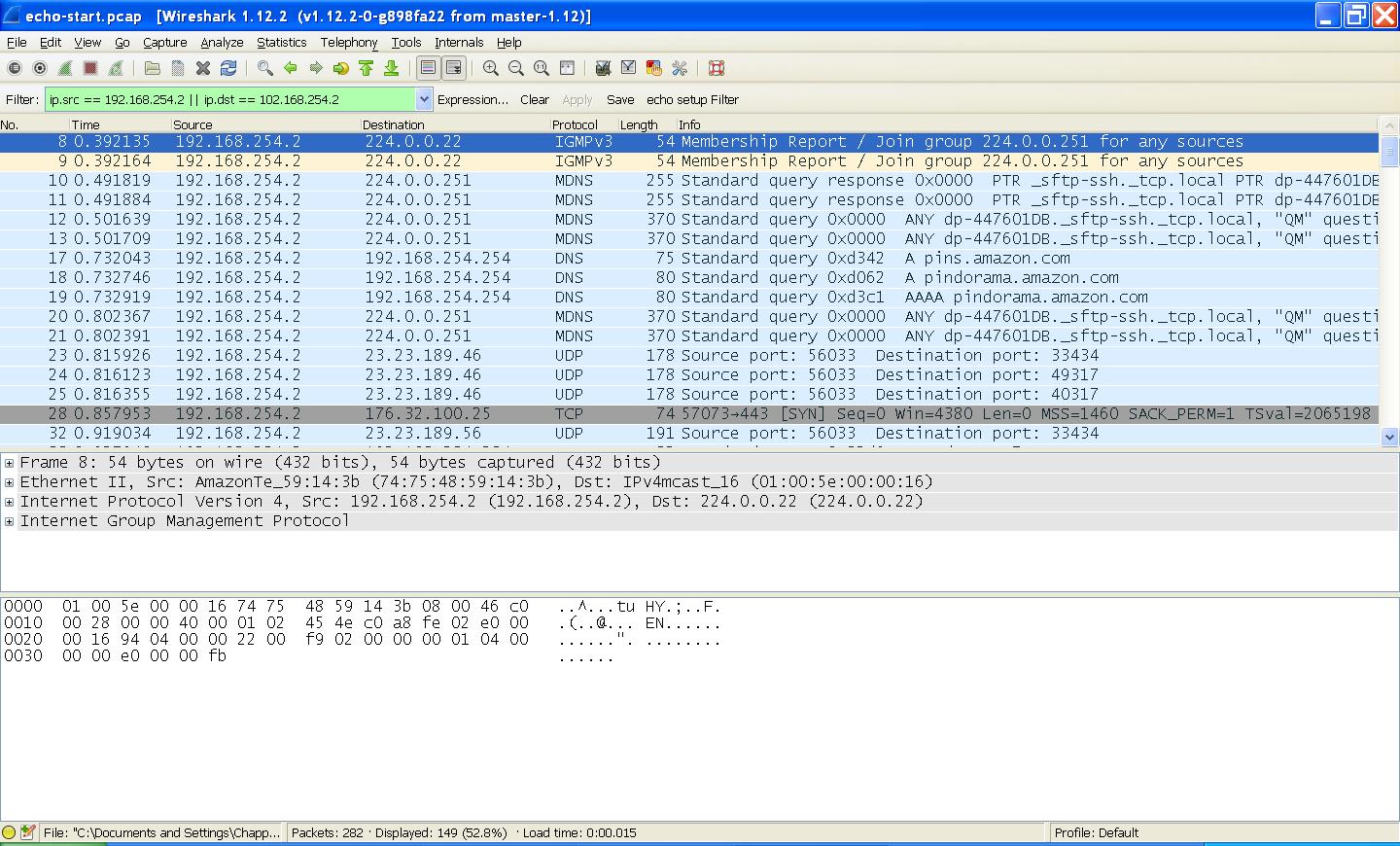
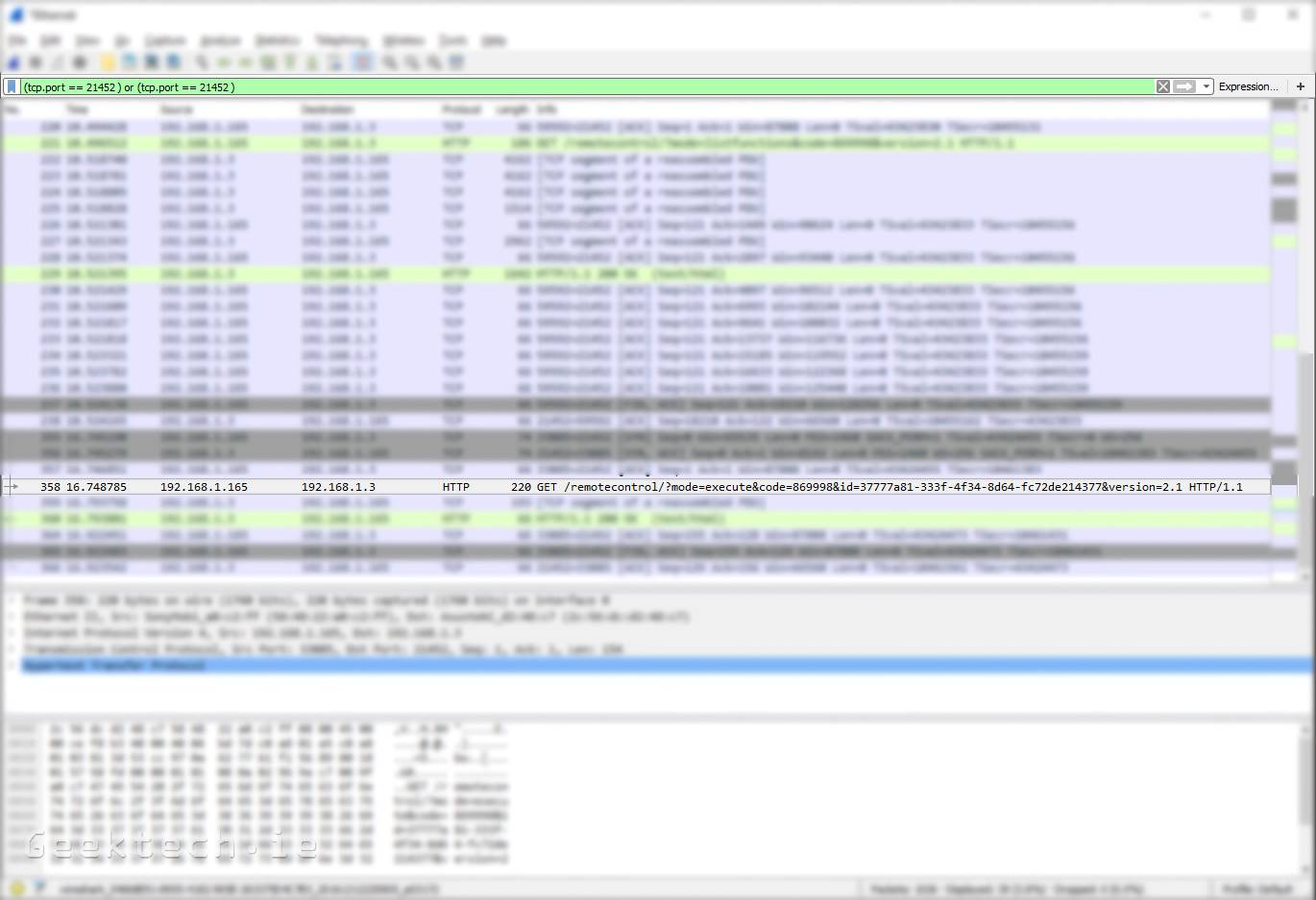
Careless Whisper: Does Amazon Echo send data in silent mode? – AV-TEST Internet of Things Security Testing Blog

Careless Whisper: Does Amazon Echo send data in silent mode? – AV-TEST Internet of Things Security Testing Blog
Introduction to TShark. Hello guys I am Sudeepa Shiranthaka and… | by Sudeepa Shiranthaka | InfoSec Write-ups

Careless Whisper: Does Amazon Echo send data in silent mode? – AV-TEST Internet of Things Security Testing Blog